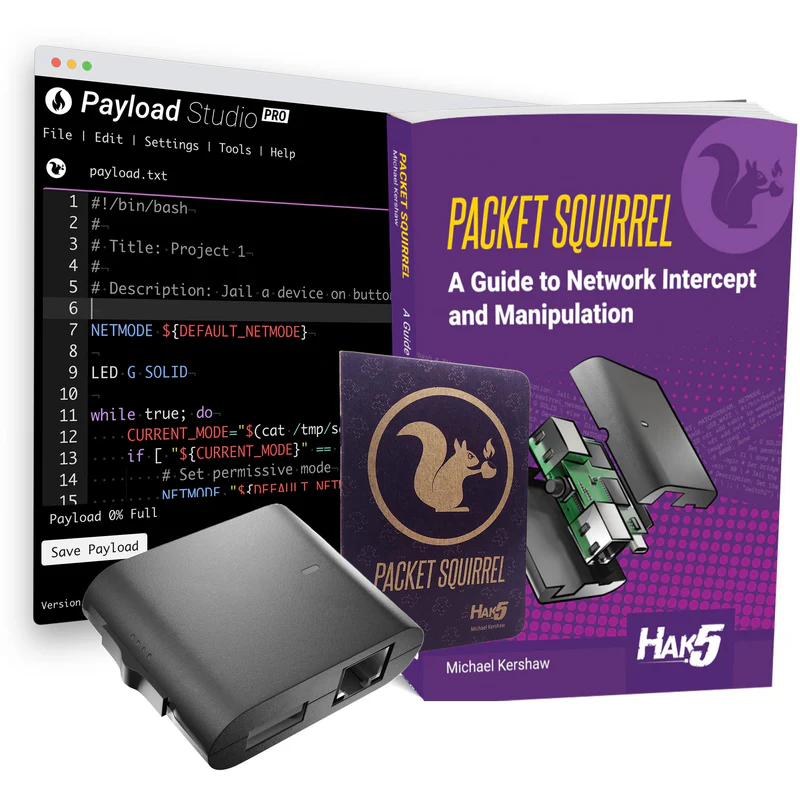
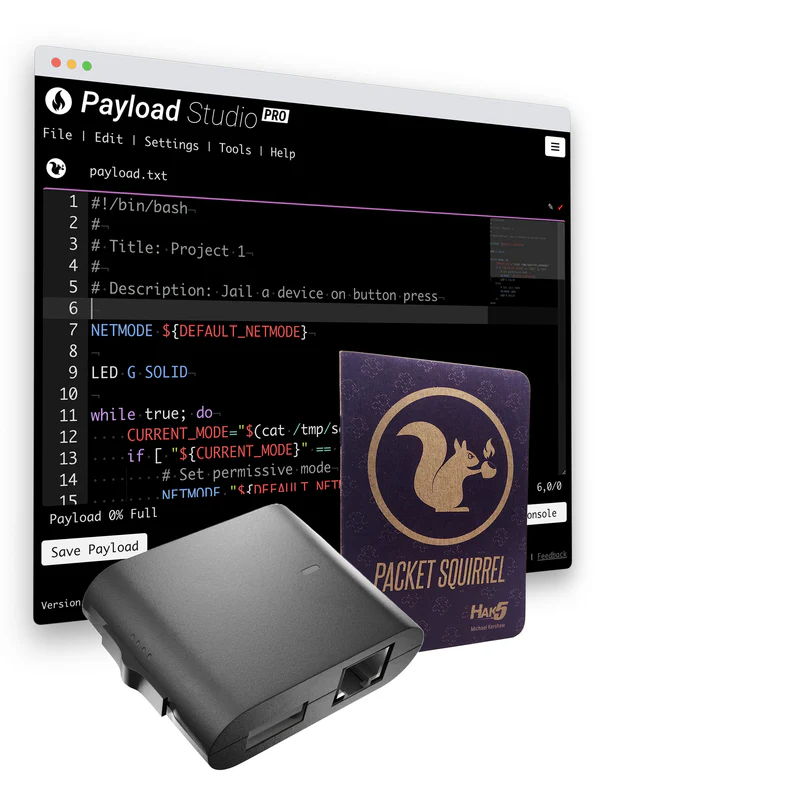
Leverage the simplicity of DuckyScript™ with the extensive capabilities of the Bash and Python scripting languages to easily craft intricate payloads.
While payloads may be written in DuckyScript alone, the complete range of programming options and commands offered by Linux enhances the possibilities even further
Man-In-The-Middle Made Easy
- Plug inline between your target and network.
- Flip the switch to select a payload.
- Connect to a USB-C power source.
That’s it! The Packet Squirrel runs your payload; from packet sniffing, to remote access, man-in-the-middle and more.
Packet Squirrel Pocket Guide
This little pocket guide packs a punch! Learn the essentials of DuckyScript and Bash for the Packet Squirrel and keep this quick-reference handy for your next payload masterpiece. Each major feature is covered along with example payload snippets.
The Hak5 Packet Squirrel Mark II is a pentesting and systems administration tool for manipulating Ethernet networks powerfully and easily.
By utilizing simple DuckyScript™ in conjunction with the extensive capabilities of the Bash scripting language, you have the ability to conveniently craft intricate payloads. While payloads may be written in DuckyScript alone, the complete range of programming options and commands offered by Linux enhances the possibilities even further.
The Packet Squirrel Mark II extends the capability of the original Packet Squirrel with more DuckyScript commands, modern tools, new VPN support, and new traffic interception, logging, and manipulation options.






Mwende (verified owner) –
Website is clean easy to navigate and secure
Cooper (verified owner) –
Finally a legit platform with no fake or scam tools
Liam (verified owner) –
Very satisfied with my purchase from this site
Elijah (verified owner) –
Finally found a trusted source for penetration testing equipment
Noah (verified owner) –
Highly recommend to any beginner or pro in cybersecurity
Mason (verified owner) –
Super impressed with the authenticity of the hacking devices offered
Liam (verified owner) –
Devices are fully functional and safe to use
Cooper (verified owner) –
Website is clean easy to navigate and secure
Wyatt (verified owner) –
Devices are fully functional and safe to use
Zoe (verified owner) –
The tools are reliable and exactly as described
Lucas (verified owner) –
Fast delivery and original products every time
Lucas (verified owner) –
I love the transparency and quality they provide
Faith (verified owner) –
Customer support was helpful and knowledgeable about every product
Grace (verified owner) –
Highly trusted website for ethical hacking kits
Elijah (verified owner) –
Highly recommend to any beginner or pro in cybersecurity
Mason (verified owner) –
Fast delivery and original products every time
Charlotte (verified owner) –
Highly trusted website for ethical hacking kits
Jackson (verified owner) –
Everything is well categorized and explained for beginners
Cooper (verified owner) –
Highly recommend to any beginner or pro in cybersecurity
Amara (verified owner) –
Highly trusted website for ethical hacking kits
Hunter (verified owner) –
Best place to shop for professional pentest tools
James (verified owner) –
Everything is well categorized and explained for beginners
Olivia (verified owner) –
Website is clean easy to navigate and secure
Wyatt (verified owner) –
This website provides the best ethical hacking tools I have ever used
Sienna (verified owner) –
I love the transparency and quality they provide
Neema (verified owner) –
Legit site with 100 percent working devices
Imani (verified owner) –
Devices are fully functional and safe to use
Grace (verified owner) –
These tools have helped me improve my cybersecurity skills